A Free OSINT Lesson: How Your "Friend with Benefits" Became an Insider Threat
The sex is great though...
This is one of those "stranger than fiction" moments, where that hook-up fun buddy suddenly becomes a nightmare "insider threat" for your employer. The sex may be great, but the operational security sucks.
Throughout my weird career, I've worked on a wide range of projects and worked for and with a lot of different people. Some friends of mine own and operate a digital forward business, which I can't name, and they've become quite successful. I occasionally help them with security issues, data breach stuff, monitoring their online situations… you get the drift.
One recent morning, I got a message on Signal from one of them. An IP address based in New Jersey repeatedly attempted to access the Admin email account. Given that this company is based in Manhattan and none of the staff reside in New Jersey, nor were scheduled to travel there, this was a fun little attempt to break in.
"We've had two attempts so far," my friend's text read.
“Ok, I’ll take a look,” I responded.
After running a search, it was clear the New Jersey IP was a VPN, and this looked like your standard attempt to simply log in. Basic shit.
What was curious, though, was how the attacker in question even knew there was an "admin" login. I ran searches in various breach data tools, and nothing popped up. My friend's firm had never experienced a leak or a breach. The "admin" logins were not online or public as far as I could tell.
Was the attacker just guessing? What's more, the IP was from Jersey, and everyone is in Manhattan. That is pretty close and indicates some level of research on behalf of our attacker. Or just dumb luck?
Intuition tells me that such a low-level attack probably came from some kid in a warehouse in China, India or North Korea trying to gain access. They probably did a bit of OSINT to find their location (though they didn't nail it). But to attempt a shot in the dark on an admin account, and a blind guess at a password? Something ain’t right.
There had to be a fresh leak. Something brand new.
It's January 2025. My friend (who messaged me on Signal about the attempted logins) is sitting, watching Netflix, in the apartment of his girlfriend. Now, I use the term "girlfriend" very loosely here. In earlier times, they would be called "lovers." In our modern and very vulgar present, the term "fuck buddies" would be more apt. A "friend with benefits."
This has been a four-month "situationship" at this point. Both are successful adults in their very early 40s who never found a long-term fit. No kids. No commitments outside of work. They were happy enough.
As they were watching Netflix on that fateful cold New York evening in January, my friend received a work email from one of the firm's partners explaining that a folder was missing a file in the company Dropbox. It wasn't an emergency, but it was pressing enough that the lovers had to pause their movie so he could upload it.
My friend, using the laptop belonging to his paramour, logs into his personal Google Drive account and downloads the missing file to her laptop. It wasn't sensitive. He then logs into the company's Dropbox account, and you guessed it, "admin@companyX.com." He uploads the file and texts his colleague, saying it's there. There is a 👍🏼 and a "Thanks!"
The movie is unpaused. The film eventually ends. Coitus.
Life goes on.
Sometime between then and now, I met this dude named Aidan Raney. He made some hilarious comment on one of my LinkedIn posts, I think, and offered to help me with a roadblock I was having on an investigation into a username that was allegedly (I have to use that word) uploading CSAM to a forum. He sent me a link to this tool he built that monitors infostealer data.
Much like breach data, infostealer data exists in that nebulous grey zone of technically stolen information that lives in public repositories online. Their use in courts or in legal matters depends on the judge and the jurisdiction, and it's not clear-cut. Lots of folks in the investigation field don't know what infostealer data even is, never mind a judge or a lawyer.
If I had to provide you a sort of pop culture metaphor, though, I'd cite Luthen Rael's monologue from Andor when he explains that, in order to fight the evil Empire, he's "condemned to use the tools of his enemy."
In the modern battle between surveillance and privacy, any tool can be used for both good and evil. A tool that can bring a CSAM network down is the same tool an asshole immigration officer with a hard-on for an orange-coloured fascist with bad hair can use to deport an innocent and legal resident to El Salvador.
Hand-wringing and pearl clutching are part of the process as we deal with any new tool in the investigations trade, and so is applying sober second thought to who gets access. This is philosophical shit, and working in the OSINT space during the current rise of fascism is complex.
I decided to dip a toe into this infostealer world. I’m the naturally curious sort. I wanted to understand what we are dealing with.
Farnsworth Intelligence is Raney’s firm, and he set me up with his toolkit.
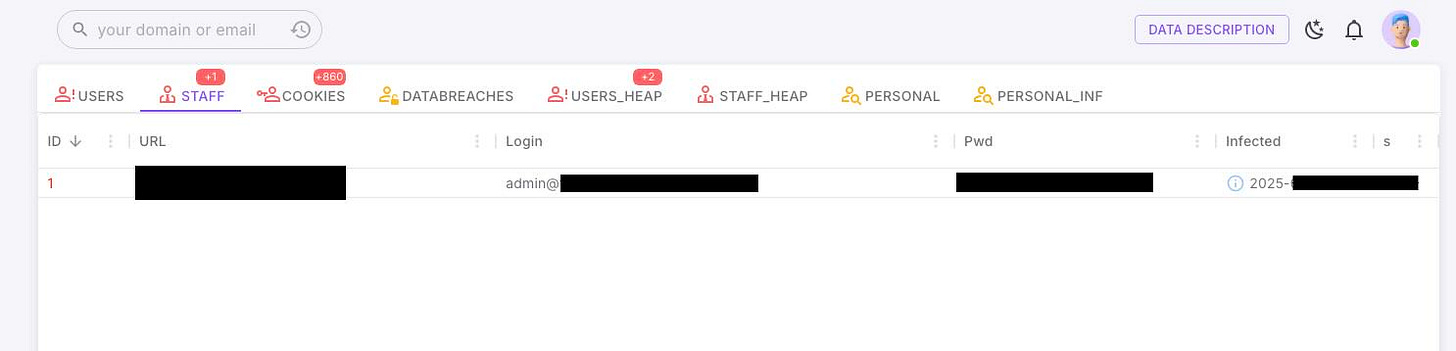
When the text came in from my friend, I had only run a couple of searches so far. This seemed like a good opportunity, so I punched in "admin@companyx.com”
And there it was. Brand new. Password and all.
But I had more questions. It was one thing to see that there was a leak, but understanding how it happened, that was what I was after.
Did a staff member at my friend's firm click a link in a janky phishing email? Did they click on some weird ass website that downloaded it to their machine? Was this an intern who downloaded the Game of Thrones porn parody from a torrent site?
Like Inigo Montoya from The Princess Bride…
Using Raney’s Infostealer data tool, I was able to see the infection itself. I could zero in on the data that was pulled from the victim’s computer and figure out why my friend’s Admin login credentials were there.
The Signal exchange…
“Hey! I found the leak. It looks like someone used your Admin login for a Dropbox account on a computer that got hacked.”
“Interesting.”
“So it looks like a recurring email on this system is ‘jane@email.com’.”(Obviously not the real email)
“WHAT."
“‘jane@email.com’ - looks like a personal computer…”
“Of fucking course.”
“Do you know this person?”
“Yeah…you could say that.”
“Well, she needs to change all her passwords. Why does she have the Admin logins?”
“THE UNKNOWN ENEMY WITHIN”
“Fuck you talkin about? Change your passwords.”
“Old girlfriend”
“Jesus”
This is less of an OSINT lesson than an operational security lesson.
No one ever suspects that a friend with benefits could be an insider threat, because of that one time you used their computer.
The wild bit is that this happens way more often than you think. The home’s family computer that your kids use to download cheats for their shitty online games become these little malware infested systems in your house. Or when your dad, who lives with you, clicks that “Your computer is infected!” link so they can fix it.
Even on the professional front, when we create logins for various services like Dropbox, Notion, or Canva, and we share those with employees or contractors, we expose ourselves on a lot of fronts.
I often tell people that those really difficult OSINT investigations become a matter of finding the slip-ups and the mistakes. You often rely on your target to make a mistake somewhere along the line, and as you gumshoe through your investigation, you come across that mistake.
While no real harm was done to my friend or his company, it was one of those fun moments that simply go to show how complicated this whole OSINT thing is. There is probably some clever “protection” and condom joke I can make here, but I won’t.