Clicking Links So You Don't Have To: Twitter Thirst-Bot Edition
Our beloved dumpster fire of a social network has a new swarm of horny bots.
Seeing someone Like your mindless Tweets feels good.
Admit it. Those little shots of dopamine when we are interacted with on social media are undeniably spicy, some would say addictive.
However, myself and probably millions of other people on Twitter1, noticed a strange phenomenon occurring on the platform the past few months. I’ll illustrate with one of my finest Twitter interactions.
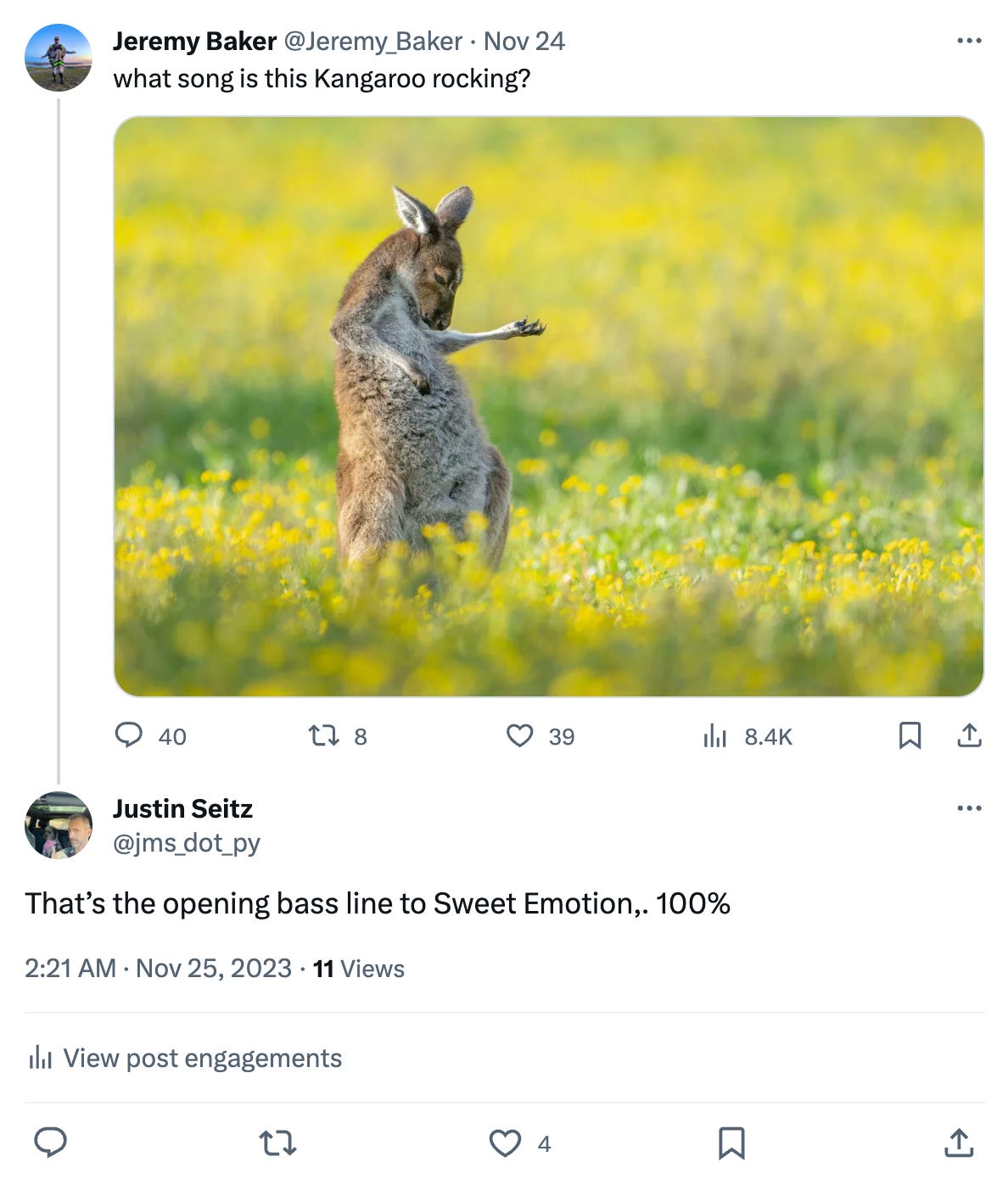
At the bottom of the screenshot it shows there are 4 total likes on that grammatically flawed drivel by yours truly. Clicking on the View post engagements link will give me a list of who, or what, liked this Tweet.
This is the pattern I had noticed, as you’ll see below. A Tweet goes out and then a handful of attractive, friendly women all just seemingly gobble it up.
Not usually the response I get on Twitter, not gonna lie:

Upon further investigation (and much to my chagrin) they all have similar username patterns, similar profile descriptions and usually link to some weird-ass domain that looks like a dating service of some kind. They aren’t my fans after all. How disappointing.
Pulling the domain name out of each profile we see three different values:
With the three profiles lined up we can quickly pick up that each of them may be connected to different domains, but all three of them use similar patterns of repeating emojis, similar profile text and two of them have nearly identical follower / following counts. I have found that many of the accounts in my feed that exhibit these booty-bot characteristics hover around the 20-21 mark for one or both values of friends and followers. My data collection on this was anecdotal at best so please don’t go citing me to CNN.
Back to the investigation.
This is all pretty weird, sure, but for Twitter it’s nothing new these days. When I run the three domains through dnsdumpster.com two of them (oddly the two with the near identical friend/follower counts) point to the same 194.147.78[.]42 address on a server in Moscow, Russia. The profile in the middle points to an Amazon IP address in the USA. If you try the domains yourself on the front page search box at dnsdumpster.com you should see the same. I am going to focus on the two in Russia.
First off, don’t get all worked up now, ya hear? Just because something appears to be hosted in Russia doesn’t mean that it is hosted in Russia. Once you confirm that it is in fact hosted in Russia, that doesn’t automagically make it a disinformation campaign or some Russian government-led operation to siphon money from unwitting North American Internet users through their weiners.
*adjusts tinfoil hat and clears throat*2
If we then take the IP address resolved for each domain and run it in the search box on the front page of dnsdumpster.com it will tell us how many domains it can find that share the same IP address. Which it turns out is a lot. Over 100 for the Moscow-based IP address, at least3. Good lord. This is a whole other investigation in itself and raises numerous other investigative and verification questions.
Secure Browsing
It’s time to hit the pavement and start clicking these suckers, it’s the only way to find out.
When I go traipsing around the filthy Internet the first thing I do is pop open a Kasm tab in my browser and start a new session. If you’ve never used Kasm, it’s an inexpensive, secure virtual computer that lives out in the ‘cloud’ which prevents me from infecting my real computer if I end up downloading malware. It has a number of other of benefits too long to list here. Once I am done browsing, my Kasm session self-destructs (this is optional) and my system at home is no worse for wear.
In this case, I simply pasted the three profile URLs into my Kasm session’s clipboard, then visited each site. In each case, it took me through a variety of forms, surveys and other pages that were covered in racy pictures that would make your Mom blush from beyond the grave. To spare you all (and my Mom, rest her soul) I didn’t capture any screenshots or video of this part.
While I was performing this research, it’s worth noting that I was browsing via a United States based IP address. Your path to booty-bot Valhalla may be different from mine depending on what country you access the dating domains from. In each case for me, after filling out the surveys or clicking on all the nudes, I landed on the same dating-slash-hookup platform called: Well Hello.
Well hello, indeed.
I’ll let the video do the rest of the talking:
As highlighted above by the illustrious Mr. DeLonge, I was equally surprised to see the company name was changing on the bottom of the payment page! That doesn’t normally happen in my experience.
It caught my eye as I was manually browsing around through each of the target sites and it again drives home the point that you simply have to have an open mind, pay a little attention (remember I am ADHD, attention is in limited supply) and you’ll be surprised what you’ll find out there.
Payment pages, privacy policy statements and terms of use documents are all golden opportunities to hunt for selectors, those unique little pieces of information that help us pivot in our investigations. Particularly booty-bot investigations.
Conclusion: Dirty Deeds
Honestly, I got tired of clicking refresh and updating the video but I truly wonder how many companies we can discover here, just by slapping that refresh button. If you refer to our Big Kahuna post, we can now run each of these companies through OpenCorporates.com to see if there are any common connections, common directors, shared addresses, all the while updating our spreadsheet of selectors or our graphs.
Now here’s the thing. Very quickly you will find people connected to these companies that are involved in a vast, labyrinthine network of companies in the United Kingdom, the United States and Cyprus. I think it is safe to say an early conclusion is that, no matter how fragile my ego may be, these accounts are giving me low quality Likes that are leading to a suspicious network of websites. These websites evenutally take us to an even more suspicious payment page that is complete with a rotating cast of company names.
It’s tempting…but I’ll have to leave it here. The family is back home, the dogs need to be fed and with a full advocacy caseload and advisory work bubbling away, it is here where I must tap out.
Feel free to pick it up where I left off…just use protection. I beg of you.
Justin
ps. Shoutout to Clare for being my editor on this one while our real editors are…where are our editors?
Resources Referenced
DNSDumpster - link
Kasm - link
OpenCorporates - link
Our Advocacy Page - link
Permanent Record Research Inc. - link
Twitter Booty Bots Backing Track (say that three times fast) - link
I refuse to call it X, fuck that.
Seriously, I am joking here. It’s a joke.
Paid subscribers please see the thread below which has a downloadable CSV of all the selectors collected here including domains, IP addresses and corporate entities, if you would like to dive down the rabbit hole yourselves.





For paid subscribers a thread has been started that has the CSV of selectors and all healthy, constructive discussion is welcome in there. Or we'll boot your ass out :)